Role-Based Access Control (RBAC) in Azure — A Complete, Real-World Explanation
If your organization uses Microsoft Azure, you’ve probably heard the phrase “Role-Based Access Control (RBAC)” thrown around in every security conversation.
But what does it actually mean? Why is it so critical for cloud security?
And how does it work behind the scenes when you give someone access to a storage account, a database, or a resource group?
Let’s unpack RBAC — not just in theory, but with a real-world story that makes it easy to remember and apply in practice.
The Core Idea
Role-Based Access Control (RBAC) in Azure is about giving the right people the right level of access — and nothing more.
In simple terms:
RBAC controls who can do what on which resources.
Azure has thousands of resources — virtual machines, databases, storage accounts, apps, networks, and more.
Not everyone should be able to delete a VM or change a firewall rule.
That’s where RBAC steps in — as the security guard that checks permissions before letting anyone in.
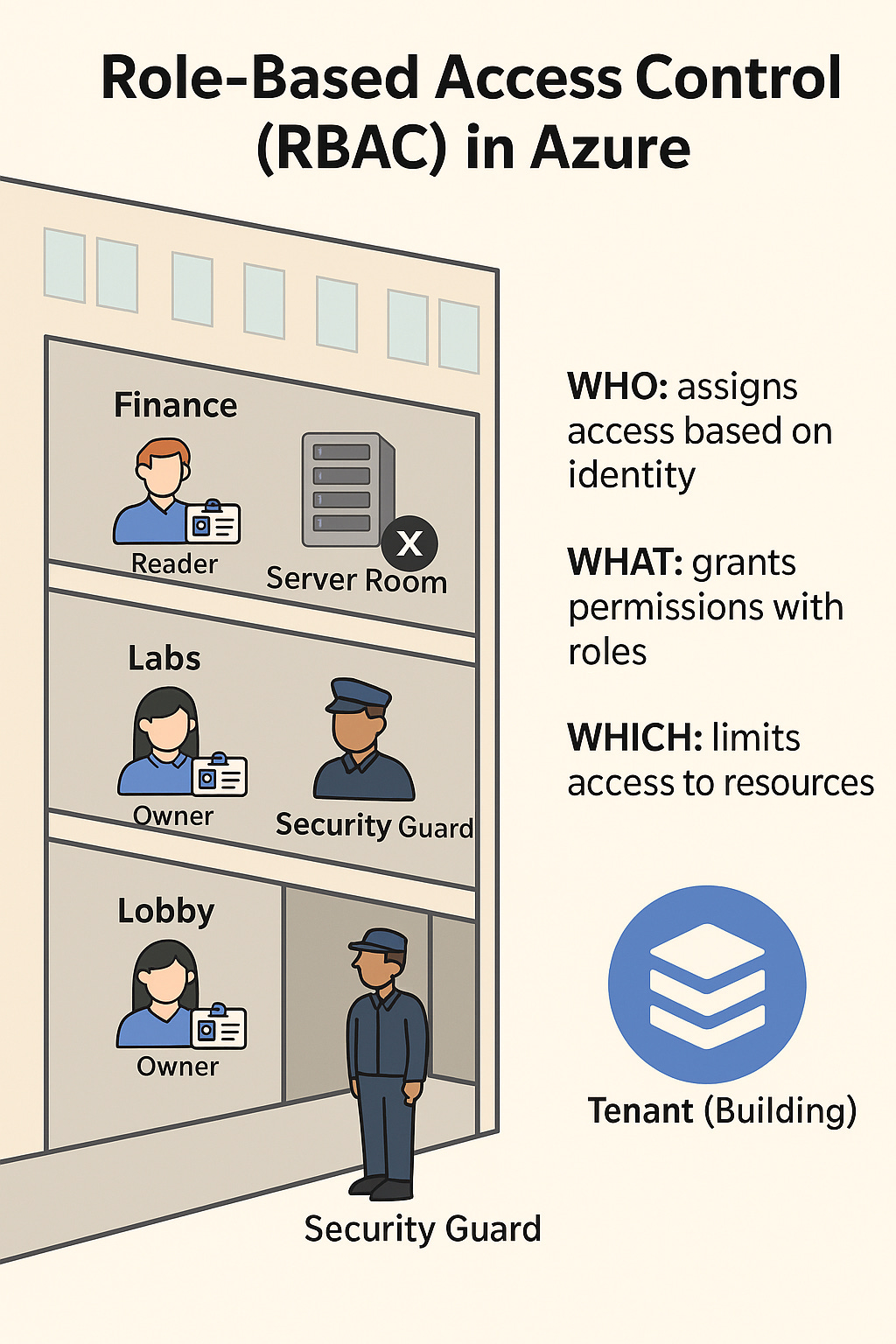
Real-World Analogy — The Corporate Office Building
Imagine your organization operates inside a massive skyscraper.
The building has hundreds of rooms — meeting halls, finance offices, labs, server rooms, and cafeterias.
Every employee gets a badge (Azure Identity).
But not all badges unlock every door.
Let’s see how RBAC fits into this analogy:
The Building (Azure Tenant)
This is your company’s entire Azure environment — where all departments (subscriptions, resource groups, and resources) live.Floors and Rooms (Azure Resources)
Each floor or room represents a specific Azure resource — like a virtual machine, database, or storage account.Badges (User or Service Principal)
Every employee, app, or service gets an identity.Access Rules (Roles)
The rules determine what you can do once you’re inside — read files, write data, modify configurations, or only observe.Security Desk (Azure Entra ID)
Before entering, everyone’s identity is verified.
Entra ID (formerly Azure AD) checks your badge and tells the door what permissions you have.Access Hierarchy (Scope)
You can assign access at different levels: the whole building, one floor, or just a single room.Tenant level → access to everything (the whole skyscraper).
Subscription level → one company division or department.
Resource group level → one specific team’s area.
Resource level → one specific room (like a single database).
How RBAC Works Internally
Azure RBAC works based on three main elements:
Security Principal — Who are you giving access to?
A user (like bhargavi@company.com)
A group (like “Finance Team”)
A service principal (an app that connects programmatically)
A managed identity (for an Azure resource like a VM or function app)
Role Definition — What actions can they perform?
Each role defines a set of allowed actions like:Read data
Write data
Delete data
Manage configurations
Azure comes with built-in roles like:
Owner
Contributor
Reader
Storage Blob Data Reader
Virtual Machine Administrator
You can also create custom roles for specific use cases.
Scope — Where does this access apply?
You can give someone access to:The whole subscription
A resource group
A single resource
Permissions cascade downward — if you give someone access at the subscription level, it applies to everything under it.
Access Evaluation — The actual check
When a user performs an action (like deleting a VM), Azure checks:The user’s identity in Entra ID
All assigned roles
Whether those roles allow the requested action within that scope
If yes — access granted ✅
If no — access denied ❌
Real Example — Applying RBAC in Action
Scenario 1: Finance Team Access to Storage
You work in an organization with one Azure subscription and multiple departments.
Finance Team stores monthly reports in a Storage Account.
IT Team manages infrastructure.
Developers deploy apps but shouldn’t touch finance data.
Here’s how you’d set it up:
Create a resource group called
RG-FinanceData.Add your finance storage account there.
Assign the “Storage Blob Data Contributor” role to the Finance Team’s group — at that resource group level.
Assign the “Reader” role to auditors, so they can view data but not modify it.
Now:
Finance can upload, edit, and delete reports.
Auditors can only read them.
Developers have no access at all.
🎯 Result: Each role has the right access, and nothing more.
Scenario 2: The Temporary Contractor
A contractor joins your company for 2 weeks to configure a few dashboards.
You assign them the “Contributor” role on only one resource group — RG-Analytics.
They can build and edit dashboards inside that resource group,
but can’t touch anything else in your environment.
When their contract ends, you remove the role assignment, and their access disappears immediately.
That’s the power of scoped access — precise and revocable.
Scenario 3: The Overpowered Owner
Let’s say an admin accidentally assigns the Owner role to a developer at the subscription level.
Now, that developer can delete resources, change configurations, or even give themselves higher permissions.
One wrong click — and your entire environment is at risk.
That’s why RBAC exists — not just to grant permissions, but to prevent dangerous over-permissions.
Role Examples in Plain Language
Owner: Full control. Can manage access and configurations. (like a department head with a master key)
Contributor: Can make changes but can’t assign access to others. (like a team leader who can modify rooms but can’t issue new badges)
Reader: View-only access. (like a guest who can walk around but can’t touch anything)
Storage Blob Data Reader: Read files from Blob Storage, nothing else. (like someone who can open a specific drawer, but can’t change what’s inside)
User Access Administrator: Manage who has access, but not modify data. (like an HR manager who decides badge permissions but doesn’t enter labs)
RBAC in a Real IT Workflow
Imagine your organization uses Azure to host applications.
The DevOps team deploys code to production servers.
The Database team manages SQL and backups.
The Networking team maintains firewalls and VNets.
The Auditors monitor compliance without touching systems.
Each team gets roles that fit their purpose:
DevOps → Contributor (on the app resource group)
DBAs → SQL Contributor
Networking → Network Contributor
Auditors → Reader
Now everyone can do their job — without stepping on each other’s toes.
🎯 It’s like a well-run company where every team has the right key for their own section — and no one wanders into another department.
Custom Roles — When Built-In Roles Aren’t Enough
Sometimes built-in roles are too broad or too limited.
Let’s say you want a user to:
Read storage accounts
Write only to specific containers
But not delete anything
You can create a custom role with exact permissions.
It’s like designing a special access badge for someone who needs to enter one lab but not the others.
Custom roles give you surgical control over your environment — a key reason enterprises love Azure RBAC.
RBAC and Azure Entra ID (Azure AD)
Under the hood, RBAC relies on Azure Entra ID for authentication.
When someone logs in, Entra ID confirms their identity.
RBAC then checks their assigned roles to see what they’re allowed to do.
In short:
Entra ID authenticates who you are.
RBAC authorizes what you can do.
Best Practices for Implementing RBAC
Follow the Principle of Least Privilege
Grant only the minimum permissions needed for a person’s job.Assign Roles to Groups, Not Individuals
Makes management simpler — add or remove users from groups instead of reconfiguring permissions.Use Built-in Roles Wherever Possible
Avoid reinventing the wheel unless necessary.Regularly Review Role Assignments
People change roles — make sure their access changes too.Monitor Role Assignments with Azure Policy or Defender for Cloud
Detect overly broad or unused permissions.Use PIM (Privileged Identity Management)
Allow temporary elevation of privileges for admins — so high access isn’t permanent.
The Bigger Picture
RBAC is one of the cornerstones of Azure’s identity and access governance model.
It ensures that access to your cloud isn’t based on “trust,” but on explicit, traceable permissions.
It brings structure, security, and accountability — so that cloud operations scale safely, without chaos.
Final Thought
Think of your Azure environment as a high-security office tower.
Everyone should be able to enter — but only into the rooms they truly need.
Role-Based Access Control is the system that makes sure:
Each badge (identity) opens only the right doors.
Permissions are easy to grant, trace, and revoke.
No one — not even the boss — walks into the wrong room accidentally.
In the world of cloud computing, RBAC isn’t just a feature — it’s your safety net.
It’s what keeps collaboration powerful, scalable, and most importantly — secure.