Kerberos Meets Scala: A Developer’s Guide to Secure, Ticket-Based Authentication in the JVM World
From mythical guard dog to modern enterprise authentication — explained with real code.
For content overview videos
https://www.youtube.com/@DotNetFullstackDev
Kerberos is everywhere in large enterprises—finance, telecom, healthcare, pharma, analytics, and government networks.
If you’re building Scala-based microservices using:
Akka HTTP
Play Framework
Apache Spark
Kafka clients
Hadoop/YARN
Distributed clusters
…you will almost certainly encounter Kerberos.
But here’s the real problem:
Most Kerberos explanations feel like reading an ancient spellbook.
Terms like TGT, SPN, KDC, AS-REQ, ticket enciphered — overwhelm new developers immediately.
So let’s rewrite this story in a way that makes sense to a real programmer.
This blog walks you through:
What Kerberos is (in simple human language)
How Kerberos works in a real enterprise
How Scala apps authenticate using Kerberos
Actual Scala code using JAAS + Kerberos principals
How Akka HTTP or Spark adopts Kerberos automatically
By the end, you’ll feel confident building Kerberized Scala services.
1. Kerberos in One Simple Analogy (No Security Jargon Needed)
Imagine a big corporate building.
You don’t type your password at every door.
Instead:
Security desk verifies you once using your ID card
They give you access stickers (tickets)
Each sticker lets you enter certain rooms
Rooms trust the sticker because security issued it
This is exactly how Kerberos works.
Security desk = Domain Controller (KDC)
Your corporate login = Kerberos principal
Access stickers = Kerberos tickets
Rooms = Scala services like Spark, Akka, Kafka
Your Scala application is a “room” that only accepts visitors with valid stickers.
2. How Kerberos Works — The Scala Developer’s Version
Kerberos uses two kinds of tickets:
TGT (Ticket Granting Ticket)
Issued when you authenticate the first time.
Service Ticket
Issued for each specific service (e.g., Kafka, Spark).
High-level flow:
User logs into the system → gets TGT
Scala application requests access to a service (e.g., Kafka broker)
TGT → exchanged for Service Ticket
Scala client sends the service ticket in every request
Service (broker/web API) validates ticket against KDC keys
No passwords go over the network.
3. Why Kerberos Matters in the Scala World
Scala is heavily used in:
Big-data platforms
Event streaming systems
Distributed computing clusters
High-security enterprise environments
These environments often run:
Hadoop / HDFS (Kerberos mandatory)
Spark on YARN
Kafka clusters with SASL/Kerberos
Akka microservices inside corporate domains
Kerberos is the first-class citizen of security in JVM ecosystems.
4. JAAS — The Bridge Between Scala and Kerberos
Scala uses the Java Authentication and Authorization Service (JAAS) under the hood.
Kerberos in Scala usually requires a JAAS config file:
jaas.conf
Client {
com.sun.security.auth.module.Krb5LoginModule required
useKeyTab=true
storeKey=true
useTicketCache=false
keyTab=”/opt/keys/scala-service.keytab”
principal=”scala-service@YOURDOMAIN.COM”;
};
This file tells the JVM:
Which principal to use
Where the keytab file is
Whether to use ticket cache
5. Authenticating with Kerberos in Pure Scala
Scala code to login using JAAS + Kerberos:
import javax.security.auth.login.{AppConfigurationEntry, Configuration, LoginContext}
object KerberosAuthDemo {
def main(args: Array[String]): Unit = {
// Load the JAAS configuration
System.setProperty(”java.security.auth.login.config”, “/opt/jaas.conf”)
System.setProperty(”java.security.krb5.conf”, “/etc/krb5.conf”)
try {
val loginContext = new LoginContext(”Client”)
loginContext.login()
println(”✔ Kerberos authentication successful!”)
println(”Authenticated principal: “ +
loginContext.getSubject.getPrincipals)
}
catch {
case ex: Exception =>
println(”❌ Kerberos authentication failed: “ + ex.getMessage)
}
}
}
What this code does:
Reads JAAS file
Fetches the principal/keytab
Asks Kerberos KDC for a TGT
Logs the principal
If authentication works, your Scala process now has a valid ticket.
6. Kerberos + Akka HTTP (Server-Side Authentication)
Akka HTTP can sit behind:
Apache/Nginx with Kerberos enabled
Or Windows AD domain reverse proxy
Kerberos usually terminates at the reverse proxy, which then forwards identity headers to Akka.
Example Akka route:
val route =
extractRequest { req =>
val user = req.headers.find(_.name == “X-Authenticated-User”)
.map(_.value)
.getOrElse(”anonymous”)
complete(s”Hello $user! You were authenticated by Kerberos.”)
}
Your reverse proxy sets:
X-Authenticated-User: DOMAIN\username
7. Kerberos + Kafka (Very Common in Scala)
If your Scala service connects to Kafka:
val props = new java.util.Properties()
props.put(”security.protocol”, “SASL_PLAINTEXT”)
props.put(”sasl.mechanism”, “GSSAPI”)
props.put(”sasl.kerberos.service.name”, “kafka”)
props.put(”bootstrap.servers”, “kafka1:9092”)
props.put(”group.id”, “my-scala-group”)
val consumer = new KafkaConsumer[String, String](props)
Kafka automatically uses JAAS + keytab to authenticate.
8. Kerberos + Apache Spark (Another Huge Use Case)
In secured Hadoop clusters:
kinit -kt spark.keytab spark-user@REALM.COM
spark-submit --principal spark-user --keytab spark.keytab job.jar
Spark obtains a TGT → then uses that to interact with:
YARN
HDFS
Hive
Kafka
Keep the Momentum Going — Support the Journey
If this post helped you level up or added value to your day, feel free to fuel the next one — Buy Me a Coffee powers deeper breakdowns, real-world examples, and crisp technical storytelling.
9. Summary — Kerberos Isn’t Hard. It Was Just Never Explained Simply.
Kerberos feels complex because it mixes:
network authentication
cryptography
AD configuration
JVM internals
But at its heart, it’s simple:
“Authenticate once → receive tickets → present tickets to Scala services.”
Scala integrates beautifully with Kerberos because:
JVM has native support
JAAS provides a simple configuration model
Frameworks like Spark, Kafka, and Akka already support it


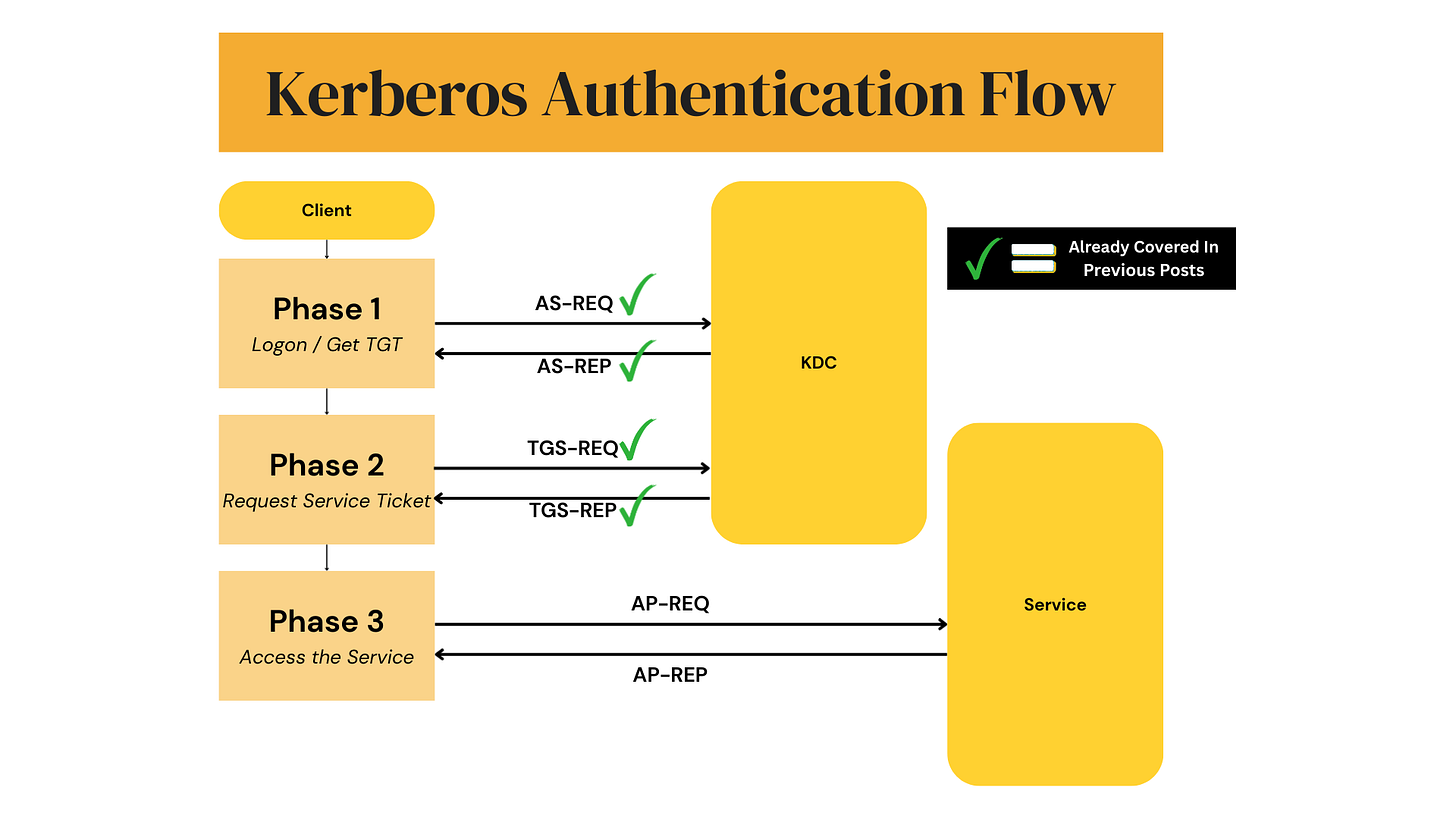
The corporate building analogy actually nailed it. JAAS always felt like this weird extra layer until you realize it's just the glue between JVM and Kerberos. Definitely bookmarking this for when I inevitably need to wire up SASL on Kafka again.